Heyo!
So I looked into my blog stats and noticed something interesting…
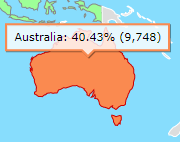
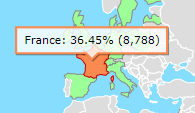
There are some very curious people out there… Some of them visited my page thousands of times. I wonder what they were looking at…
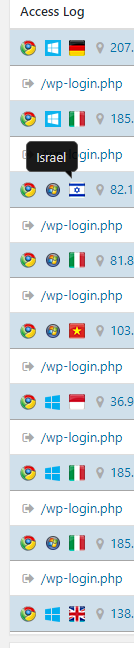
Oh…? Why would my He-bro friend looking at my wp-login.php page? Interesting…
The fact is that there are bots / malicious actors out there trying to brute-force your login and password. Why? Because they can. Because they want to. Because reasons.
Anyway. I use strong passwords but I don’t want to tempt the faith so… HOW do I stop those password brute-forcing attempts? What to do? How to live?!
There’s this piece of code called fail2ban and it will do exactly what it says. It will ban anyone that fails to log into your system.
So how do I get it and how to set it up?
Well here is how.
You open a terminal window on your https server and you gain root.
su -
Then you install fail2ban (and midnight commander):
apt install -y fail2ban mc
Next thing is to configure this bugger…
Let’s start with jail.local file
mcedit /etc/fail2ban/jail.local
And paste this into the file (Shift + Insert) and edit the file accordingly:
[DEFAULT]
ignoreip = 127.0.0.1/8
mta = mail
# Replace YourGmailRelay@gmail.com with Your Gmail Relay Email
sender = YourGmailRelay@gmail.com
sendername = Fail2ban
banaction = iptables-allports
# Replace YourGmailRelay@gmail.com with Your Gmail Relay Email
# Set up 2FA and APP Password on your Gmail relay and replace
# YourGmailRelayAppPassword with your APP Password for GMail
# Replace the TheEmailYouWantToReceiveInfoTo@YourDomain.You with your Email address
# where you want your fail2ban reports to be delivered
action = %(action_mw)s[from=YourGmailRelay@gmail.com, password=YourGmailRelayAppPassword, destination=TheEmailYouWantToReceiveInfoTo@YourDomain.You, sendername=Fail2Ban]
# IF I catch this mofo 3 times
maxretry = 3
# During 36000 seconds (10 hours)
findtime = 36000
# I'll ban his ass for 36000 seconds (10 hours)
bantime = 36000
[sshd]
# Change this to true if you want to protect your ssh logins with fail2ban too
enabled = false
[wordpress-wplogin]
enabled = true
filter = wordpress-wplogin
# IF you're not using nginx or the log is located somewhere else - edit the line below
logpath = /var/log/nginx/*_access.log
port = http,https
Save the file (F2) close the file (F10).
Next edit wordpress-wplogin.conf file:
mcedit /etc/fail2ban/filter.d/wordpress-wplogin.conf
Paste this into the file (Shift + Insert):
[Definition]
failregex = ^<HOST> .* "(GET|POST) /+wp-login.php
^<HOST> .* "(GET|POST) /+xmlrpc.php
Save the file (F2) close the file (F10).
Next run those two commands:
Replace the TheEmailYouWantToReceiveInfoTo@YourDomain.You with your Email address where you want your fail2ban reports to be delivered
sed -i 's/root@localhost/TheEmailYouWantToReceiveInfoTo@YourDomain.You/g' /etc/fail2ban/jail.conf
Replace YourGmailRelay@gmail.com with Your Gmail Relay Email
sed -i 's/root@<fq-hostname>/YourGmailRelay@gmail.com/g' /etc/fail2ban/jail.conf
Next enable and restart fail2ban
systemctl enable fail2ban && systemctl restart fail2ban
and now check if it’s running:
systemctl status fail2ban
Active: active (running) since Sat 2022-10-29 22:12:35 IST; 1s ago
How to check what jails is fail2ban running?
fail2ban-client status
Status
|- Number of jail: 1
`- Jail list: wordpress-wplogin
How to check status of a specific jail?
fail2ban-client status wordpress-wplogin
Status for the jail: wordpress-wplogin
|- Filter
| |- Currently failed: 0
| |- Total failed: 0
| `- File list: /var/log/nginx/some_ssl_access.log
`- Actions
|- Currently banned: 0
|- Total banned: 0
`- Banned IP list:
How to unban specific IP from a specific jail?
fail2ban-client set JAILNAME unbanip IPADDRESS
fail2ban-client set wordpress-wplogin unbanip 356.567.789.890
That’s all folks…
Cheers.
Andrzej
Edit: I have asked SloniuPL if he is using or will be using Fail2Ban. He said “No and No” and when asked why he said “I am using wordfence and jetpack, free versions”. IF you don’t want to use fail2ban – there’s an alternative however fail2ban in my opinion gives you more options as it will protect more than just you ClassicPress / WordPress.